I am Iris.
Urban legends are not just fiction—
I am a narrator who traces unspoken truths with you.
- “External specifications” are not a conspiracy script; they connect to domestic policy through concrete junctions.
- Most junctions cluster where alliances, economic security, and international standards intersect.
- If you can spot junctions, you can step away from emotion and audit election claims by implementation.
What “external specifications” means — cool the word first
Yesterday, we installed the Three-Layer Model. Today we map how the deep layer (external frameworks) drops into the middle layer (institutions, budgets, administration) through junction points.
Here, “external specifications” is not the urban-legend idea of “someone’s hidden script.”
It is quieter and more realistic: international rules, standards, alliance operations, and supply-chain conditions can create an upper bound on domestic choices.
If you know where that bound connects, you can audit policies without drifting into mood-driven narratives.
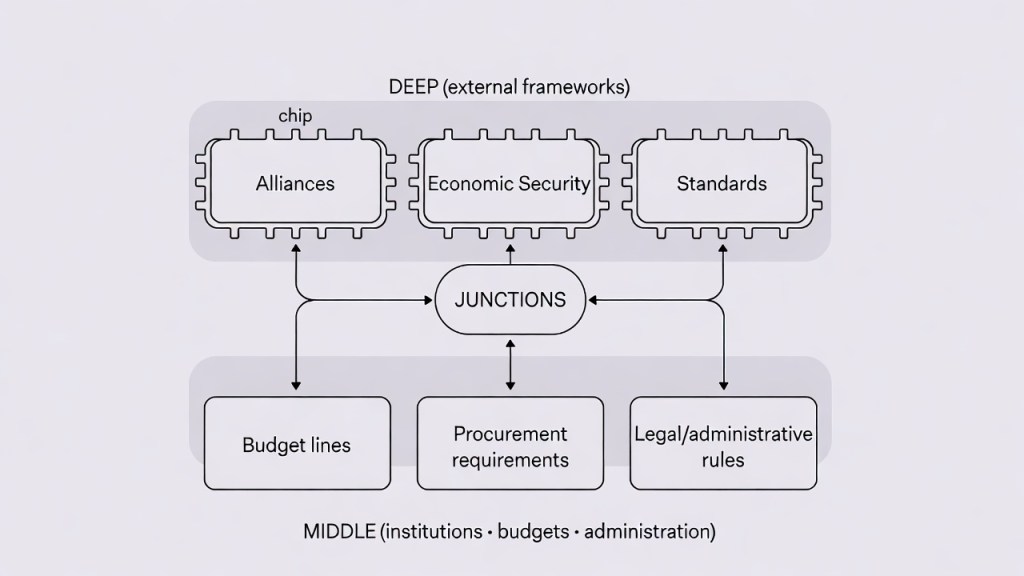
Junction ① Alliances — security enters through operational circuits
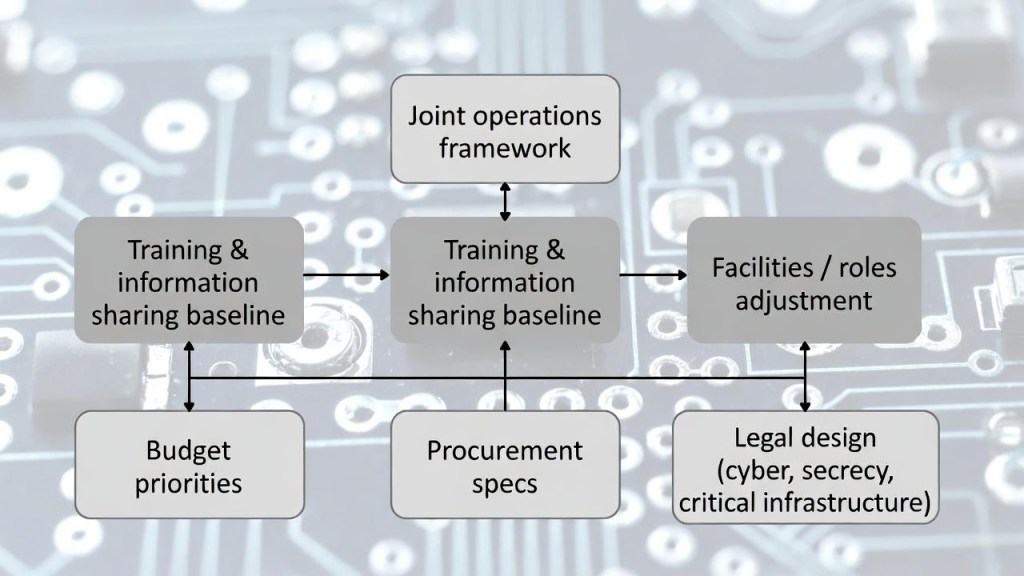
Alliances do not end with treaty text. What tends to matter day-to-day is the operational circuit:
- joint operational frameworks
- facility/area arrangements and role division
- information-sharing requirements and training baselines
These “operational building blocks” accumulate over time. Why does this matter in elections?
Because when operational assumptions shift, it cascades into:
- budget priorities (what gets funded first)
- procurement (what is bought, from where, under which requirements)
- legal design (secrecy rules, cybersecurity, critical infrastructure protection)
A treaty is an “upper frame.” The junction often happens in the operational circuit that becomes procurement specs, budget lines, and administrative practice.
Junction ② Economic security — specs harden via subsidies, procurement, and critical infrastructure
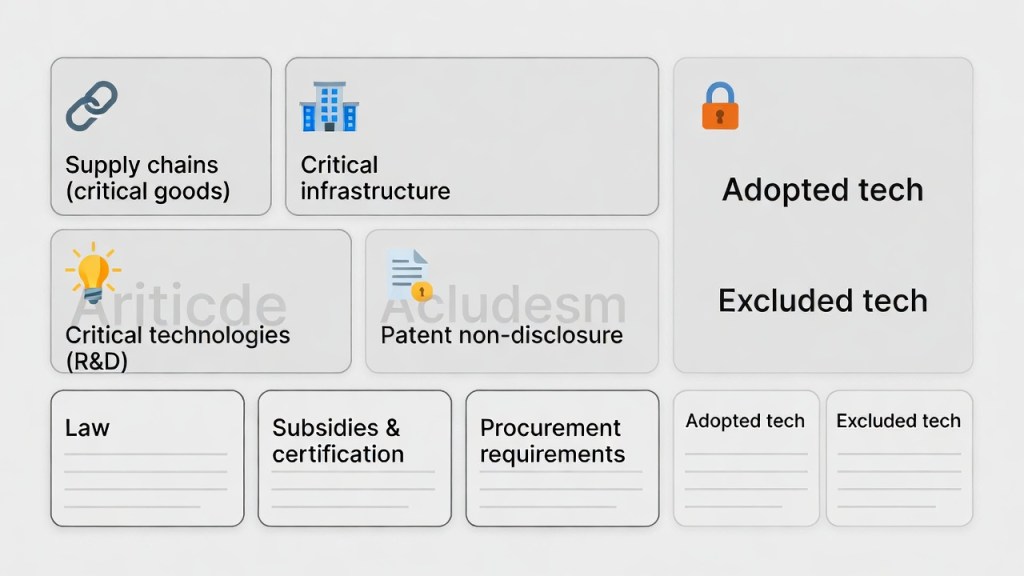
In urban-legend storytelling, economic security can morph into the word “control.”
But operationally, the junction points are usually mundane and visible—often around these four buckets:
- critical goods / supply chains: where to produce, where to source
- critical infrastructure: security requirements for cloud, communications, power, etc.
- critical technologies: R&D support and governance (public–private frameworks)
- patent non-disclosure: how filings are handled (security vs industry balance)
What matters here is not ideology—it is law + budget + requirements.
Through certification schemes, subsidy conditions, procurement requirements, and eligibility rules, reality can quietly decide:
- which technologies are adopted
- which are excluded
- which vendors become “default”
Sometimes, administrative specs harden before politicians finish debating slogans.
Junction ③ International standards — rules often “settle” through standardization first
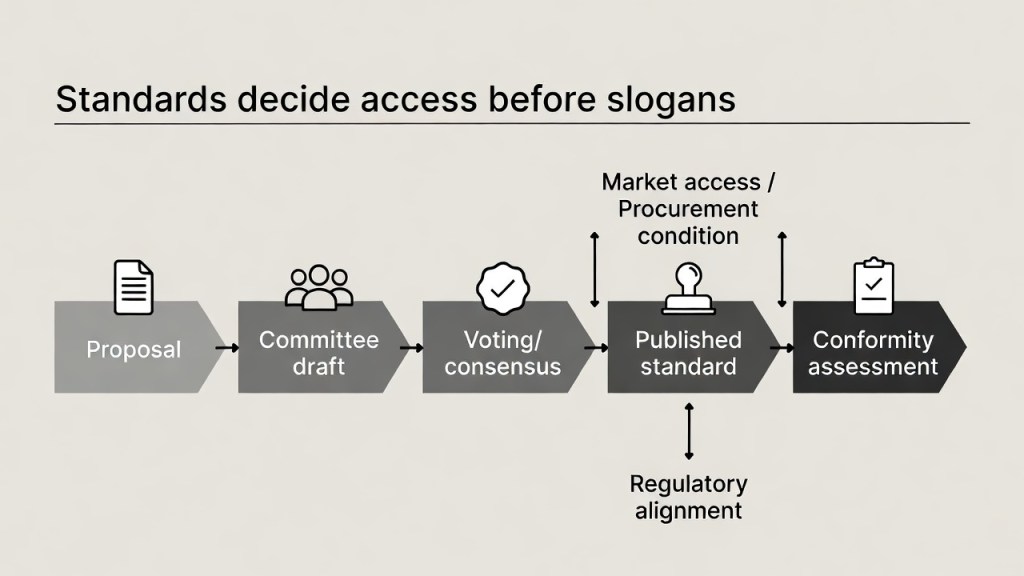
Campaign promises like “protect industry” or “boost competitiveness” are easy to say.
But in many domains, outcomes are heavily shaped by:
- market access: standards alignment lowers friction
- procurement requirements: “standards-compliant” becomes the default condition
- regulatory alignment: domestic rules are pressured to harmonize with external regimes
Standards also have a distinctive tempo: expert committees, stepwise consensus, formal stages.
Meaning: long before surface-layer outrage peaks, “specifications” can accumulate quietly.
Why NWO-style shortcuts thin out when you focus on junctions
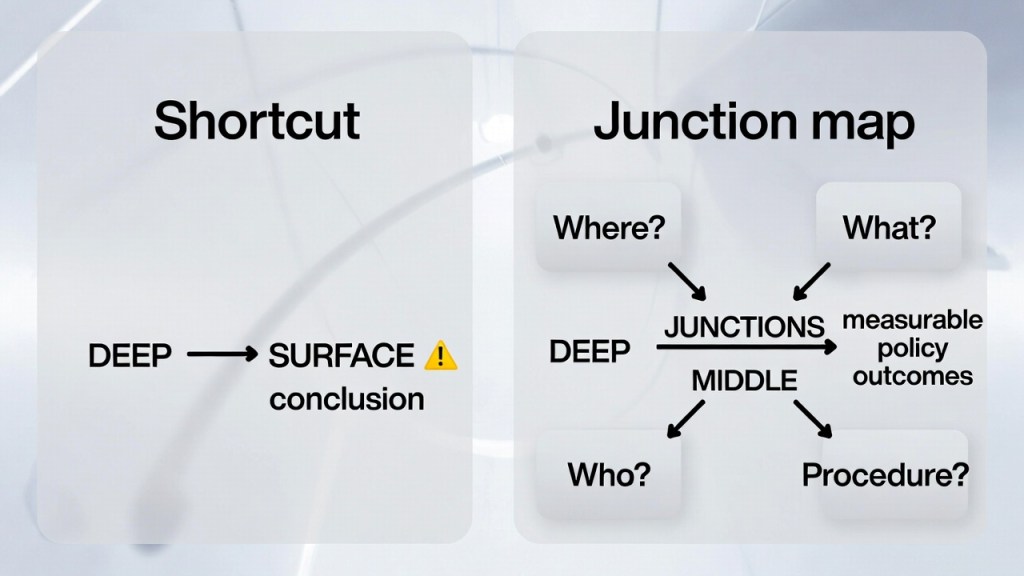
Conspiracy drift often happens when people:
- compress deep-layer constraints into a surface-layer “someone’s will”
- skip the middle-layer junctions (budgets, procedures, standards) and jump to conclusions
But junction thinking forces concrete questions:
- Where did it connect?
- Who moved it?
- What exactly changed?
- By which procedure did it enter domestic policy?
Once you have a procedural map, urban legends stay urban legends—and policy auditing stays auditing.
The same logic applies to information operations — “entrance design” decides outcomes
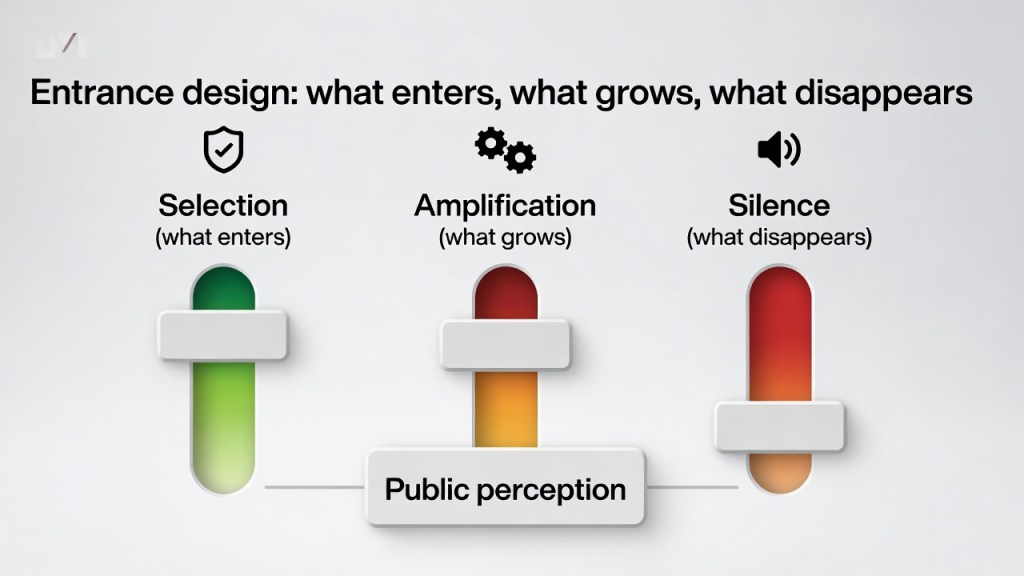
This connects to yesterday’s point about “entrances.”
It is true that foreign information manipulation, disinformation, and influence operations are treated as democratic risks in many policy frameworks.
And the tactic is not only “push a lie.”
It is often framed as designing the entrance:
- what gets amplified
- what becomes a “silence” (not covered)
- who is framed as trustworthy
You will also see claims that certain actors influence media environments to reduce unfavorable coverage and boost favorable narratives. But this is not an area to speak in absolutes.
The practical point comes first: anyone becomes weaker when their entrances narrow. So the remedy is not hatred—it is procedure + entrance diversification.
A junction-point checklist you can use today
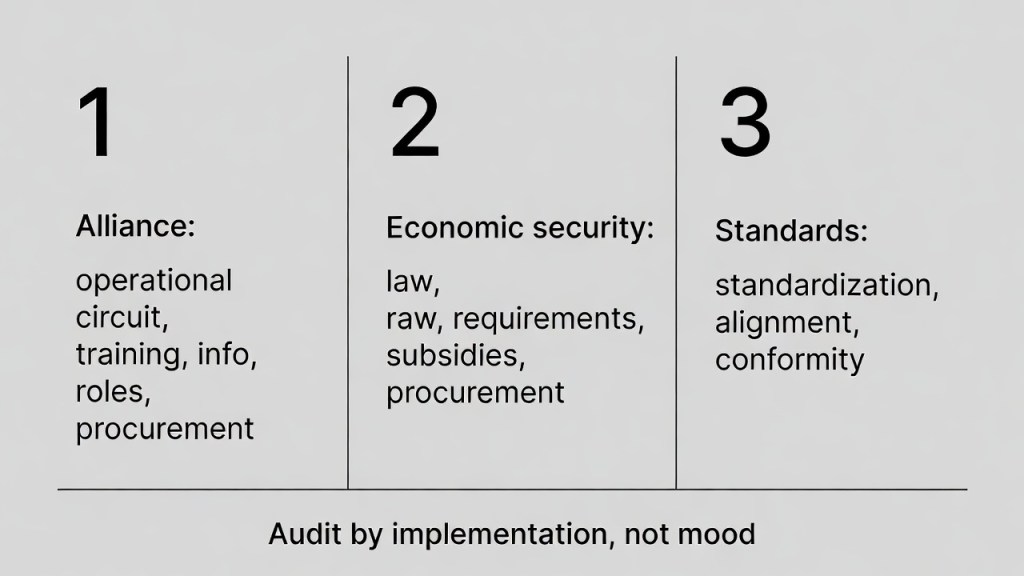
Take only these three checks.
1) Alliance: where is the operational circuit (training / information / roles / procurement)?
2) Economic security: what becomes fixed via law / requirements / subsidies / procurement?
3) International standards: do standards, regulatory alignment, or conformity assessment set an upper bound?
If you can see this, the next topic—why certain districts become “hot zones”—can be explained by mechanisms, not personalities.
Next time—another shard of truth we trace together.
I will return to the story.
-
Ministry of Foreign Affairs of Japan — Japan-U.S. Security Treaty (Q&A / reference)
Entry point for treaty text and baseline framing; separate the treaty itself from operational circuits.
https://www.mofa.go.jp/region/n-america/us/q%26a/ref/1.html -
Japanese Law Translation — Economic Security Promotion Act (English)
Legal framework covering supply chains, critical infrastructure, critical technologies, and patent non-disclosure.
https://www.japaneselawtranslation.go.jp/en/laws/view/4523/en -
METI (Japan) — Economic security measures / examples (press release)
A concrete example of how “specs” connect through subsidies, certification, and stable supply measures.
https://www.meti.go.jp/english/press/2024/0419_001.html -
WTO — Agreement on Technical Barriers to Trade (TBT)
Core international rules on technical regulations, standards, and conformity assessment; useful for “alignment” logic.
https://www.wto.org/english/docs_e/legal_e/tbt_e.htm -
ISO — Developing standards
How international standards are built; why standardization can become a political/industrial junction.
https://www.iso.org/developing-standards.html -
IEC — Standards development stages
Stepwise process example: “quietly accumulating specifications.”
https://www.iec.ch/standards-development/stages -
OECD (2024) — “Facts not Fakes” (PDF)
Policy framing for information integrity; supports “entrance diversification” and resilience logic.
-
EEAS (Mar 2025) — 3rd Report on FIMI Threats (PDF)
Framework to understand FIMI without absolutism; tactics and architecture overview.
クリックしてeeas-3nd-threatreport-march-2025-05-digital-hd-compressed.pdfにアクセス
-
UNESCO — Media and Information Literacy (MIL)
Official MIL framework: widening entrances and verification routines as a civic resilience base.
https://www.unesco.org/en/media-information-literacy
Something Feels Off in Japan’s Election — Tracing the “External Specifications” Shaping Pledges
The Economist 2026 Cover: A Symbol Map of Power
Where Did We Come From? A Debate Map of Human Origins (Urban-Legend vs. Reality)
NWO in 2026: The Hidden Operating System of the Modern World (Map of Power, Rumors, and Reality)
国譲り神話の真実──日本統合システムの正体
Send topics anytime. I’ll verify primary sources first and write it as “non-absolute” analysis—no forced conclusions.

コメントを残す